Making business means taking risks. Risk management deals with exposures to specific threats that can take advantage of existing vulnerabilities and affect organisations. Enterprise risk management (ERM) consists of the processes used to manage risks in the enterprise.
Strategic (not defining and meeting objectives), market (negative interactions with the market), credit (exposure to non-payments) and operational risk (exposure to loss from internal processes, people, systems and external events) constitute ERM.
An ERM umbrella that is aligned with the business strategy helps the organisation achieve its objective.
Information is an essential asset for most organisations: it connects all risk management disciplines and, more broadly, most business processes use it. Information risk management, also called information security, is an element of operational risk.
There is a current tendency towards linking the information security activity (infosec) with the operational risk management (ORM) practice and, more generally, with the enterprise risk management activity.
The link between infosec and ORM disciplines can eventually play a positive role in constructing sustainable and superior benefits for organisations.
An overarching model is proposed to understand and manage the complexity of infosec and ORM in organisations: the ‘risk house’ model.
This model explains how to link the infosec practice with the ORM strategy and practice. It locates ORM within ERM and signals the pervasiveness of information and the need to develop information security and to link it with ORM.
The infosec-ORM link should always happen in accordance to the risk appetite of the organisation. ORM objectives can be significantly facilitated if both risk disciplines are aligned with the strategy of the organisation to achieve its objective.
A survey of 82 experts provides two main conclusions: First, management commitment, the degree of development of information security and the alignment of risk management with the business strategy (i.e. its strategic alignment) are strongly related to superior benefits achieved in organisations.
Second, the three most probable superior benefits achieved are stakeholder value, new business opportunities and better compliance. These three benefits ultimately contribute to the responsible image of the organisation.
Introduction
Doing business is taking risks to achieve an objective while following a strategy.
All activities in an organisation should be aligned with the business strategy so that the organisation achieves its objective. However, nowadays it is frequent to find big companies, let alone small and medium ones, handling risks in a very archaic and fragmented way, not aligned with the organisation’s strategy.
It is usual that unrelated groups deal with related dimensions of enterprise risk: credit, market, strategic, operational and also reputational risk. This is a very ineffective and inefficient way to manage risk.
Credit and market risk management models are well established and developed (e.g. VaR). They fall outside the scope of this study. This study investigates the level of development of infosec and operational risk management practices within organisations and justifies why enterprise risk management needs to be aligned with the organisation’s strategy.
On one hand, the recent succession of corporate and government scandals happening in the First World (Enron, Arthur Andersen, Shell, Worldcom to mention only a few of an endless list of well known names) has created a myriad of corporate governance regulations that organisations have to comply with. This new corporate governance scenario includes better ways to deal with risk in organisations.
On the other hand, the increasing dependence on information and on information systems for most organisations makes the role of information security increasingly pivotal. The Internet revolution and open systems architectures bring an extraordinary level of connectivity and interaction but also the great challenge to guarantee information security in organisations.
This study looks at both hot topics from a linking and reconciling angle: operational risk management (ORM) and information security (infosec). Based on the fact that both information and operational risk spread throughout the whole organisation, this study defends that the systematic link of the infosec practice with the ORM strategy and practice bring superior benefits to the organisation.
Furthermore, it presents a way to carry out this linkage between infosec and ORM, which is anchored in a proposed model, the ‘risk house’: a comprehensive model to understand and manage risks in organisations.
A survey was launched to research the relationship between the level of evolution in infosec and risk management within organisations and potential benefits that organisations enjoy. These benefits will help organisations to better achieve their objectives, managing risks while following their strategy.
The survey in turn follows the spirit of the ‘risk house’ model.
82 risk management professionals from the 5 continents have answered it in a valid way. The results of the quantitative research prove the applicability of the proposed ‘risk house’ model. They serve to confirm which requirements to link infosec with ORM actually contribute to provide organisations with superior benefits. Simultaneously, they hint the pace companies nowadays follow to implement them.
All activities in an organisation should be aligned with the business strategy so that the organisation achieves its objective. However, nowadays it is frequent to find big companies, let alone small and medium ones, handling risks in a very archaic and fragmented way, not aligned with the organisation’s strategy.
It is usual that unrelated groups deal with related dimensions of enterprise risk: credit, market, strategic, operational and also reputational risk. This is a very ineffective and inefficient way to manage risk.
Credit and market risk management models are well established and developed (e.g. VaR). They fall outside the scope of this study. This study investigates the level of development of infosec and operational risk management practices within organisations and justifies why enterprise risk management needs to be aligned with the organisation’s strategy.
On one hand, the recent succession of corporate and government scandals happening in the First World (Enron, Arthur Andersen, Shell, Worldcom to mention only a few of an endless list of well known names) has created a myriad of corporate governance regulations that organisations have to comply with. This new corporate governance scenario includes better ways to deal with risk in organisations.
On the other hand, the increasing dependence on information and on information systems for most organisations makes the role of information security increasingly pivotal. The Internet revolution and open systems architectures bring an extraordinary level of connectivity and interaction but also the great challenge to guarantee information security in organisations.
This study looks at both hot topics from a linking and reconciling angle: operational risk management (ORM) and information security (infosec). Based on the fact that both information and operational risk spread throughout the whole organisation, this study defends that the systematic link of the infosec practice with the ORM strategy and practice bring superior benefits to the organisation.
Furthermore, it presents a way to carry out this linkage between infosec and ORM, which is anchored in a proposed model, the ‘risk house’: a comprehensive model to understand and manage risks in organisations.
A survey was launched to research the relationship between the level of evolution in infosec and risk management within organisations and potential benefits that organisations enjoy. These benefits will help organisations to better achieve their objectives, managing risks while following their strategy.
The survey in turn follows the spirit of the ‘risk house’ model.
82 risk management professionals from the 5 continents have answered it in a valid way. The results of the quantitative research prove the applicability of the proposed ‘risk house’ model. They serve to confirm which requirements to link infosec with ORM actually contribute to provide organisations with superior benefits. Simultaneously, they hint the pace companies nowadays follow to implement them.
Hypothesis
- Survey results corroborate that the strongest relationship exists between ‘management commitment’ to implement a risk management framework and any possible benefit for the organisation.
- The second and third most important pre-conditions for benefits are ‘infosec development’ and ‘strategic alignment in RM’ i.e. establishing an infosec programme to improve security management enterprise-wide and align all risk management activities with the strategy of the organisation.
- The development of all risk management related fields within the organisation brings benefits to the organisation. Specifically, this is the case for infosec, ERM and ORM.
- The second and third most important pre-conditions for benefits are ‘infosec development’ and ‘strategic alignment in RM’ i.e. establishing an infosec programme to improve security management enterprise-wide and align all risk management activities with the strategy of the organisation.
- The development of all risk management related fields within the organisation brings benefits to the organisation. Specifically, this is the case for infosec, ERM and ORM.
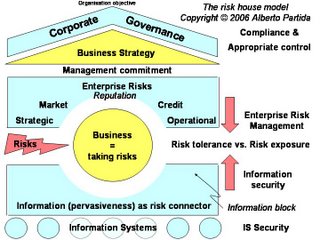
The risk house model
The risk house model. Copyright (C) 2006, Alberto Partida
The conclusion of the literature review is the proposal of an overarching enterprise risk management model: the ‘risk house’.
This model helps answering how companies can link their information security practice with their operational risk management strategy and practice to achieve superior benefits and helps understanding the results of the survey.
---------------------------------------------------------------------------------
Copyright (c) 2006 Alberto Partida.
Permission is granted to copy, distribute and/or modify this document
under the terms of the GNU Free Documentation License, Version 1.2
or any later version published by the Free Software Foundation;
with no Invariant Sections, no Front-Cover Texts, and no Back-Cover
Texts. A copy of the license is available at the GNU
Free Documentation License site.
---------------------------------------------------------------------------------
The ‘risk house’ model connects all subjects visited in the literature review. It is a comprehensive way to explain what risk means for an organisation. The core of the house is the business idea.
Every business idea brings intrinsically the need to address risks. The ideas of doing business and taking risks both are actions that constitute the core of the ‘risk house’. Managing risks is strongly coupled with the strategy of the business to achieve its objective. This is the reason why these three elements share a different background colour (yellow).
The remaining building blocks of the ‘risk house’ (sharing the blue colour) are related to risk. Surrounding the core of the ‘risk house’ (the business), there is an upper element consisting of all possible enterprise risks (i.e. strategic, market, credit and operational risks).
All of them form part of the enterprise risk block.
Reputational risks are written with a different font but they are located in the same enterprise risk block. The subtle difference is that reputational risk can be present in all four types of risks.
Information is the lower complementary block surrounding the business core. As identified in the literature review, information acts as a risk connector for all these risks. Information is pervasive. Based on the findings of the literature review, all risk practices should use a common language.
These days information resides in information systems. This is the reason why the information block lays upon several information systems. These are drawn as definite circles because organisations still struggle to integrate their information systems. It is frequent to find unlinked information systems for different business processes, bringing sometimes even more complexity to the business.
On the top of the house, corporate governance is the roof aiming at safeguarding the future of the organisation, taking care of the overall steering principles and governance processes of the organisation and its compliance with current regulations.
On the right hand side, the model refers to risk management processes related to the adjacent house element. Following a top-down approach and starting from the corporate governance umbrella, the first process related to corporate governance and business strategy is compliance and control.
The process dealing with all the risks affecting the business is enterprise risk management. Similarly, the process guaranteeing the effectiveness of information as a pervasive element that connect risks is information security.
Information systems security guarantees the confidentiality, integrity and availability of information residing in information systems.
Every process relies on the one located just below, in such a way that their seamless integration provides a unique way for the organisation to achieve its objective in the form of superior benefits.
The remaining elements of the ‘risk house’ model bring actions: Risks, as threats taking advantage of vulnerabilities, are always menacing the business. Consequently, enterprise risk management and information security provide required input to assess the current risk exposure and to compare it with the organisation’s risk tolerance (risk appetite).
This is the reason why it is so important to integrate ERM with infosec (and within ERM, especially ORM). This way, the ERM and the information blocks can determine which risks can be accepted and which risks need to be mitigated.
The last element to mention is management commitment. This is the fluid glue that links business strategy with ERM. Management commitment is essential to keep the house protected and governed.
The application of the ‘risk house’ model to different industrial sectors would show very different levels of block strength e.g. the financial world is currently one of the most advanced in terms of risk management.
The final objective of the ‘risk house’ model is to show graphically the need to protect the business by integrating risk management practices under the ERM umbrella and linking them with information security to adjust the organisation’s risk exposure with its risk tolerance.
This way, the organisation will enjoy superior benefits that will leverage achieving its objective. This is the message of the ‘risk house’ model.
The answer to the research question pops out by feeding the ‘risk house’ model, created out of the literature review, with the results obtained in the survey.
First, the indispensable glue among all blocks is management commitment, without it the ‘risk house’ would collapse.
Second, the information block and the information security process need to be assembled and maintained.
Third, the enterprise risk block and, consequently, all blocks in the house, need alignment with the business strategy.
The conclusion of the literature review is the proposal of an overarching enterprise risk management model: the ‘risk house’.
This model helps answering how companies can link their information security practice with their operational risk management strategy and practice to achieve superior benefits and helps understanding the results of the survey.

---------------------------------------------------------------------------------
Copyright (c) 2006 Alberto Partida.
Permission is granted to copy, distribute and/or modify this document
under the terms of the GNU Free Documentation License, Version 1.2
or any later version published by the Free Software Foundation;
with no Invariant Sections, no Front-Cover Texts, and no Back-Cover
Texts. A copy of the license is available at the GNU
Free Documentation License site.
---------------------------------------------------------------------------------
The ‘risk house’ model connects all subjects visited in the literature review. It is a comprehensive way to explain what risk means for an organisation. The core of the house is the business idea.
Every business idea brings intrinsically the need to address risks. The ideas of doing business and taking risks both are actions that constitute the core of the ‘risk house’. Managing risks is strongly coupled with the strategy of the business to achieve its objective. This is the reason why these three elements share a different background colour (yellow).
The remaining building blocks of the ‘risk house’ (sharing the blue colour) are related to risk. Surrounding the core of the ‘risk house’ (the business), there is an upper element consisting of all possible enterprise risks (i.e. strategic, market, credit and operational risks).
All of them form part of the enterprise risk block.
Reputational risks are written with a different font but they are located in the same enterprise risk block. The subtle difference is that reputational risk can be present in all four types of risks.
Information is the lower complementary block surrounding the business core. As identified in the literature review, information acts as a risk connector for all these risks. Information is pervasive. Based on the findings of the literature review, all risk practices should use a common language.
These days information resides in information systems. This is the reason why the information block lays upon several information systems. These are drawn as definite circles because organisations still struggle to integrate their information systems. It is frequent to find unlinked information systems for different business processes, bringing sometimes even more complexity to the business.
On the top of the house, corporate governance is the roof aiming at safeguarding the future of the organisation, taking care of the overall steering principles and governance processes of the organisation and its compliance with current regulations.
On the right hand side, the model refers to risk management processes related to the adjacent house element. Following a top-down approach and starting from the corporate governance umbrella, the first process related to corporate governance and business strategy is compliance and control.
The process dealing with all the risks affecting the business is enterprise risk management. Similarly, the process guaranteeing the effectiveness of information as a pervasive element that connect risks is information security.
Information systems security guarantees the confidentiality, integrity and availability of information residing in information systems.
Every process relies on the one located just below, in such a way that their seamless integration provides a unique way for the organisation to achieve its objective in the form of superior benefits.
The remaining elements of the ‘risk house’ model bring actions: Risks, as threats taking advantage of vulnerabilities, are always menacing the business. Consequently, enterprise risk management and information security provide required input to assess the current risk exposure and to compare it with the organisation’s risk tolerance (risk appetite).
This is the reason why it is so important to integrate ERM with infosec (and within ERM, especially ORM). This way, the ERM and the information blocks can determine which risks can be accepted and which risks need to be mitigated.
The last element to mention is management commitment. This is the fluid glue that links business strategy with ERM. Management commitment is essential to keep the house protected and governed.
The application of the ‘risk house’ model to different industrial sectors would show very different levels of block strength e.g. the financial world is currently one of the most advanced in terms of risk management.
The final objective of the ‘risk house’ model is to show graphically the need to protect the business by integrating risk management practices under the ERM umbrella and linking them with information security to adjust the organisation’s risk exposure with its risk tolerance.
This way, the organisation will enjoy superior benefits that will leverage achieving its objective. This is the message of the ‘risk house’ model.
The answer to the research question pops out by feeding the ‘risk house’ model, created out of the literature review, with the results obtained in the survey.
First, the indispensable glue among all blocks is management commitment, without it the ‘risk house’ would collapse.
Second, the information block and the information security process need to be assembled and maintained.
Third, the enterprise risk block and, consequently, all blocks in the house, need alignment with the business strategy.
Outcome of the survey: Demographics
The survey received 82 valid answers until 27 August 2006. The survey in Spanish received 8 valid answers and the survey in English 74 valid answers. Out of the 82 valid respondents, 60 (73% respondents) provided a an email address to receive the results of the study.
Question 1: Position title
Over 63% of respondents work in the information security or IS security field. Almost 21% of respondents occupy ‘other’ positions in the organisation (see figure 19); this provides a general organisation-wide perspective to answers given to the survey and possibly contributes to the variability of some answers. Overall, there is a balanced variety of positions represented in the answers.
Question 2: Seniority in current position
Close to 60% of survey participants have more than 3 year experience in their position. As a minimum, survey answers represent more than 220 years of experience.
Question 3: Field of expertise of previous position
68% of respondents come from the information technology field. Answers given show how currently information security positions are mainly filled by IT professionals and, at a lesser extent, by auditors. In addition, this percentage shows the recent creation of information security positions in organisations: only around 12% of respondents occupied an information security or risk management position before their current position.
Only above 3% of respondents come from a financial position. This indicates the current difficulty information security professionals have to use concepts like return on security investment (ROSI) and quantitative risk measurement.
Question 4: Position respondents report to
Information security is not only an information systems agenda topic. Although more than 30% respondents still report to the CISO, almost 20% of respondents report to the organisation’s CEO or Board.
In addition, almost 9% of participants report to a security officer and 13% to the chief auditor. This may show a trend to link information security either with corporate security (responsible for IT, physical security and, sometimes, business continuity) or audit.
These answers show that risk management integration has not brought a common reporting line yet: only 3% report to a chief RM officer and only 2% to a financial officer.
Question 5: Scope of influence (number of employees influenced by their work)
About 40% of respondents influence between 100 to 1000 employees. The number of influenced staff is rather balanced in the survey answers.
It is remarkable that 13% respondents influence less than 100 employees. This is a new phenomenon: Information security positions are starting to appear in small companies.
Question 6: Sector of the organisation
More than half of the respondents work in the financial sector. This is a key element to consider when discussing results. Almost a quarter of the surveyed professionals work in ICT-related industries. Utilities and government are represented only with 3% and 2% of respondents and the rest of sectors represent close to 20% of answers.
Question 1: Position title
Over 63% of respondents work in the information security or IS security field. Almost 21% of respondents occupy ‘other’ positions in the organisation (see figure 19); this provides a general organisation-wide perspective to answers given to the survey and possibly contributes to the variability of some answers. Overall, there is a balanced variety of positions represented in the answers.
Question 2: Seniority in current position
Close to 60% of survey participants have more than 3 year experience in their position. As a minimum, survey answers represent more than 220 years of experience.
Question 3: Field of expertise of previous position
68% of respondents come from the information technology field. Answers given show how currently information security positions are mainly filled by IT professionals and, at a lesser extent, by auditors. In addition, this percentage shows the recent creation of information security positions in organisations: only around 12% of respondents occupied an information security or risk management position before their current position.
Only above 3% of respondents come from a financial position. This indicates the current difficulty information security professionals have to use concepts like return on security investment (ROSI) and quantitative risk measurement.
Question 4: Position respondents report to
Information security is not only an information systems agenda topic. Although more than 30% respondents still report to the CISO, almost 20% of respondents report to the organisation’s CEO or Board.
In addition, almost 9% of participants report to a security officer and 13% to the chief auditor. This may show a trend to link information security either with corporate security (responsible for IT, physical security and, sometimes, business continuity) or audit.
These answers show that risk management integration has not brought a common reporting line yet: only 3% report to a chief RM officer and only 2% to a financial officer.
Question 5: Scope of influence (number of employees influenced by their work)
About 40% of respondents influence between 100 to 1000 employees. The number of influenced staff is rather balanced in the survey answers.
It is remarkable that 13% respondents influence less than 100 employees. This is a new phenomenon: Information security positions are starting to appear in small companies.
Question 6: Sector of the organisation
More than half of the respondents work in the financial sector. This is a key element to consider when discussing results. Almost a quarter of the surveyed professionals work in ICT-related industries. Utilities and government are represented only with 3% and 2% of respondents and the rest of sectors represent close to 20% of answers.
Outcome of the survey: Interpretation
Question 1 and 2: Position title and time in position
The position of Information Security Manager is progressively appearing in organisations. This fits with answers to questions 1 and 2: almost 25% of respondents are responsible either for information security or for IS security. In question 2, more than 64% of answerers have been less than 5 years in their position.
Question 3 and 4: Field of expertise in previous position and position to report to
As information is a valuable asset and it resides in information systems, it is plausible that 68% of respondents come from the information technology field and that still 30% of them report to the CISO. Nevertheless, this also explains the difficulty to provide information security with a business dimension.
Questions 5 & 6: Number of influenced employees and sector
Small companies are far from tackling risk management aspects: Information security and risk management professionals work for medium to large companies (only 13% of answers influence less than 100 employees) and probably in the financial sector (as more than 50% of survey respondents). This fits with the state of art in infosec and with the ERM concept, with origin in the financial sector.
Statements 1, 3 & 4
IT is transforming business processes (83% of answers) and they are frequently changing (47% of answers) together with changes in management structures (64% of answers). These results corroborate the reasons for risk management integration proposed in the literature review: changes bring complexity.
Statements 6 to 19: Information security practice
Regarding information security, the results of the survey confirm the current status presented in the literature review, still far away from effectiveness: only half of respondents perform risk analysis based either on business impact or threat and vulnerability analysis. This means that one of the key success factors for infosec, following a standard, is not present in half of the surveyed organisations.
However, some signs suggest that organisations are heading into the right direction: almost in 70% of the cases, information owners receive their risk analysis although, in 44% of the occasions, they don’t have an active role accepting or mitigating risks.
Another key success factor presented in the literature review that is not yet followed by the majority of surveyed organisations is communicating the business value of infosec (in 58% of the cases the security policy is not communicated to all employees).
Regarding the existence of infosec executive committees, in 75% of the cases they are accountable for implementing infosec controls and only in 23% of the cases they have an overall accountability for infosec. This is a characteristic of the infosec gap mentioned in the review.
Finally, only 40% of answers show collaboration between infosec and IS security. This is an integration requirement. Consequently, there is still a long way to achieve the benefits of integrating risk management fields.
Statements 2 and 5: strategic RM with employees’ involvement and transparency practice
Results follow requirements present in the review. An ERM integration requirement is to ensure everybody’s involvement. 65 % of surveyed professionals agreed theoretically with this requirement. The transparency practice requirement is followed by a surprisingly high figure of respondents: 85%
Statements 20 to 22: Acceptable risk messages
In 61% of the cases, management provided organisations with a message regarding acceptable and non-acceptable risks. This is a promising figure considering that it is a key ERM requirement to integrate infosec with ORM. However, further communication activities are required since only in 22% of the cases this message is documented and it is rarely accessible by employees (19% of answers).
Statements 17 and 18: ORM executive committee
Principle 8 of Basel II mentioned in the literature review recommends to have an effective operational risk framework in place. As operational risk permeates through the whole organisation, it is thinkable that an executive committee should be in charge of it, similarly to what ISO (2005) proposes for infosec.
However, only 48% of respondents answered positively for the ORM model and the figure is even lower when referring to the implementation of an ORM model (31%).
Statements 6 to 8 and 13
According to the survey, the information security programme set by management is more a long-term set of objectives (67% of answers) rather than middle-term (52%).
Management commitment is an essential requisite to pursue any risk management integration. However, only 42% of survey answers showed management commitment to infosec. As an example, only in 41% of cases management approved the security policy.
Statements 31 to 33: Strategic alignment for RM, infosec and IS Security
Survey results show that alignment between business strategy and infosec has been achieved in 57% of the cases whereas answers for RM (47%) and IS Security (39%) are lower.
Although these statements are not a cluster in terms of reliability to reflect a common dimension, their answers confirm first, the pervasiveness of information and second, the understanding that information is a valuable asset which must be protected.
Statements 23 to 30 and 34 to 38: tactical, strategic and organisational benefits
Increase stakeholder value, new business opportunities and better governance appear in the top 3 benefit ranking.
In addition, the organisational benefits brought in by the RM practice in the surveyed organisations have obtained lower agreement rates than the same organisational benefits brought in by the infosec practice.
Finally, the fact that 68% of respondents state that their risk management activities will be more coordinated in the future confirms the statement that organisations need and are willing to implement an integrated risk management approach, not only to be compliant but also to cope with globalisation and complexity.
The position of Information Security Manager is progressively appearing in organisations. This fits with answers to questions 1 and 2: almost 25% of respondents are responsible either for information security or for IS security. In question 2, more than 64% of answerers have been less than 5 years in their position.
Question 3 and 4: Field of expertise in previous position and position to report to
As information is a valuable asset and it resides in information systems, it is plausible that 68% of respondents come from the information technology field and that still 30% of them report to the CISO. Nevertheless, this also explains the difficulty to provide information security with a business dimension.
Questions 5 & 6: Number of influenced employees and sector
Small companies are far from tackling risk management aspects: Information security and risk management professionals work for medium to large companies (only 13% of answers influence less than 100 employees) and probably in the financial sector (as more than 50% of survey respondents). This fits with the state of art in infosec and with the ERM concept, with origin in the financial sector.
Statements 1, 3 & 4
IT is transforming business processes (83% of answers) and they are frequently changing (47% of answers) together with changes in management structures (64% of answers). These results corroborate the reasons for risk management integration proposed in the literature review: changes bring complexity.
Statements 6 to 19: Information security practice
Regarding information security, the results of the survey confirm the current status presented in the literature review, still far away from effectiveness: only half of respondents perform risk analysis based either on business impact or threat and vulnerability analysis. This means that one of the key success factors for infosec, following a standard, is not present in half of the surveyed organisations.
However, some signs suggest that organisations are heading into the right direction: almost in 70% of the cases, information owners receive their risk analysis although, in 44% of the occasions, they don’t have an active role accepting or mitigating risks.
Another key success factor presented in the literature review that is not yet followed by the majority of surveyed organisations is communicating the business value of infosec (in 58% of the cases the security policy is not communicated to all employees).
Regarding the existence of infosec executive committees, in 75% of the cases they are accountable for implementing infosec controls and only in 23% of the cases they have an overall accountability for infosec. This is a characteristic of the infosec gap mentioned in the review.
Finally, only 40% of answers show collaboration between infosec and IS security. This is an integration requirement. Consequently, there is still a long way to achieve the benefits of integrating risk management fields.
Statements 2 and 5: strategic RM with employees’ involvement and transparency practice
Results follow requirements present in the review. An ERM integration requirement is to ensure everybody’s involvement. 65 % of surveyed professionals agreed theoretically with this requirement. The transparency practice requirement is followed by a surprisingly high figure of respondents: 85%
Statements 20 to 22: Acceptable risk messages
In 61% of the cases, management provided organisations with a message regarding acceptable and non-acceptable risks. This is a promising figure considering that it is a key ERM requirement to integrate infosec with ORM. However, further communication activities are required since only in 22% of the cases this message is documented and it is rarely accessible by employees (19% of answers).
Statements 17 and 18: ORM executive committee
Principle 8 of Basel II mentioned in the literature review recommends to have an effective operational risk framework in place. As operational risk permeates through the whole organisation, it is thinkable that an executive committee should be in charge of it, similarly to what ISO (2005) proposes for infosec.
However, only 48% of respondents answered positively for the ORM model and the figure is even lower when referring to the implementation of an ORM model (31%).
Statements 6 to 8 and 13
According to the survey, the information security programme set by management is more a long-term set of objectives (67% of answers) rather than middle-term (52%).
Management commitment is an essential requisite to pursue any risk management integration. However, only 42% of survey answers showed management commitment to infosec. As an example, only in 41% of cases management approved the security policy.
Statements 31 to 33: Strategic alignment for RM, infosec and IS Security
Survey results show that alignment between business strategy and infosec has been achieved in 57% of the cases whereas answers for RM (47%) and IS Security (39%) are lower.
Although these statements are not a cluster in terms of reliability to reflect a common dimension, their answers confirm first, the pervasiveness of information and second, the understanding that information is a valuable asset which must be protected.
Statements 23 to 30 and 34 to 38: tactical, strategic and organisational benefits
Increase stakeholder value, new business opportunities and better governance appear in the top 3 benefit ranking.
In addition, the organisational benefits brought in by the RM practice in the surveyed organisations have obtained lower agreement rates than the same organisational benefits brought in by the infosec practice.
Finally, the fact that 68% of respondents state that their risk management activities will be more coordinated in the future confirms the statement that organisations need and are willing to implement an integrated risk management approach, not only to be compliant but also to cope with globalisation and complexity.
Literature review: Thinking path
1. Risk management and strategic alignment
2. Standard-based definitions of risk and risk management
3. Enterprise risk management
4. Compliance. Corporate governance
5. Compliance regulation examples: SOX and Basel II
6. Risk management silos
7. Information connects risks
8. Critical success factors for information security
9. State of art in information security
10. Operational risk management (ORM)
11. Reasons for the integration. Why the link?
12. Integration requirements for the infosec-ORM link. How to link?
13. Organisational, strategic and tactical benefits of the link
14. Top management commitment. Management innovation
2. Standard-based definitions of risk and risk management
3. Enterprise risk management
4. Compliance. Corporate governance
5. Compliance regulation examples: SOX and Basel II
6. Risk management silos
7. Information connects risks
8. Critical success factors for information security
9. State of art in information security
10. Operational risk management (ORM)
11. Reasons for the integration. Why the link?
12. Integration requirements for the infosec-ORM link. How to link?
13. Organisational, strategic and tactical benefits of the link
14. Top management commitment. Management innovation
Literature references
Aabo, Tom, Fraser, John R.S., Simkins, Betty J. (2004). The rise and transformation of the chief risk officer: a success story on enterprise risk management. Version of December 10, 2004. Revised version available in Journal of Applied Corporate Finance, Winter 2005. Pages 1-34, Available from: http://www.gloriamundi.org/detailpopup.asp?ID=453057237 [Accessed 16 April 2006]
Alvarez, Gene (2005). ‘An Operational Risk Management Framework’. Chapter 11 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 227-236.
Andersen, Arthur (2001). Basel and operational risk: new perspectives, new challenges. Financial services (March 2001). Pages 1-6.
Appel, Willie (2005). ‘Redefining IT Governance Readiness’, Meta Group, Meta Practice 2369. Pages 1-8.
Basel Committee on Banking Supervision. Risk Management Group. Cole, Roger (chairman) et. al. (2003). ‘Sound practices for the management and supervision of operational risk’, Bank for International Settlements (BIS). Pages 2-5 and 8.
Birchall, David, Ezingeard, Jean-Noël and McFadzean, Elspeth (2003). Information security. Setting the boardroom agenda. Grist and Henley Management College sponsored by Qinetiq. Executive summary also referenced. Pages 1-51.
Birchall, David, Ezingeard, Jean-Noël and McFadzean, Elspeth (2004). Information assurance. Strategic alignment and competitive advantage. Grist and Henley Management College sponsored by Qinetiq. Executive summary also referenced. Pages 1-73.
Bolton, Nick; Berkey, Judson (2005). ‘Aligning Basel II Operational Risk and Sarbanes-Oxley 404 Projects’. Chapter 12 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 237-246.
Booker, Robert (2006). ‘Re-engineering enterprise security’, Computers & Security 25. 13-17
Carey, Allan (2005). ‘2005 Global information security workforce study’, IDC whitepaper, sponsored by ISC2. Pages 1-28.
COBIT. IT Governance Institute (2000). ‘Control objectives for information and related technologies’ COBIT, 3rd edition. Pages 1-12.
Coles, Robert S. and Moulton, Rolf (2003). ‘Operationalizing IT risk management’,
Computers & Security 0167-4048/03. Pages 487-492.
Committee of Sponsoring Organisations of the Treadway Commission COSO (2004). Enterprise Risk Management Framework – Executive summary – Exposure Draft for Public Comment (pages 1-103) downloadable from www.coso.org/publications.htm
DeLotto, R., McKibben, D. and Leskela, L. (2003). ‘Risk management in the new regulatory environment’, Gartner, Research note 19 March 2003. COM-19-4409. Pages 1-4.
Dierick, Frank; Pires, Fatima; Scheicher, Martin; Spitzer, Kai Gereon (2005). ‘The new Basel capital framework and its implementation in the European Union’ [online]. European Central Bank (ECB) Occassional Paper Series no. 42 December 2005. Pages 1-28. Available at http://www.ecb.int/pub/pdf/scpops/ecbocp42.pdf [Last accessed 12 May 2006].
Dillon, Robin L. and Paté-Cornell, Elisabeth (2005). ‘Including technical and security risks in the management of information systems: a programmatic risk management model’. Systems engineering. 8. 1. Regular paper. Pages 15, 17, 18 and 24.
Ernst&Young (2005). Ernst & Young’s 8th annual Global Information Security Survey [online]. Pages 1-28. Available from: http://int.sitestat.com/ernst-and-young/international/s?Global-Information-Security-survey-2005&ns_type=pdf [Last accessed 8 May 2006]. Press release Available at http://www.ey.com/GLOBAL/content.nsf/International/Press_Release_-_2005_Global_Information_Security_Survey [Last accessed 8 May 2006]
Expansión (2006). “El libro abierto de Basilea II”. Published 30 June 2006. Page 20.
Ezingeard, Jean-Noël (2003). ‘Expert advice’ [online]. Available at http://www.infoconomy.com and http://www.information-age.com/article/2003/june/expert_advice . Security perspective [Last accessed 18 December 2005]. Pages 1-2.
Ezingeard, J.-N., M. Bowen-Schrire, et al. (2004). Triggers of Change in Information Security Management. ISOneWorld Conference, Las Vegas, Information Institute (http://www.information-institute.org/). Pages 1-37.
Fujii (2005). ‘Building Scenarios’. Chapter 7 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 169-178.
Giraud, Jean-Rene (2005a). ‘Managing hedge funds’ exposure to operational risks’. Chapter 14 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 275-283.
Giraud, Jean-Rene (2005b). ‘Managing hedge funds’ operational risks’. Chapter 14 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 284-294.
Giraud, Jean-Rene (2005c). ‘Quantifying hedge funds’ operational risks’. Chapter 14 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 295-303.
Hamel, Gary (2006). ‘The Why, What and How of Management Innovation’. Harvard Business Review. February 2006. Pages 1-12.
Hughes, Peter (2005). ‘Using transactional data to measure operational risk’. Chapter 1 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 3-12.
Huijgens, Hennie (2004). ‘Value chain control – An IT control approach that puts business in the centre’. Information systems control journal. 2 57-62.
Information Security Forum ISF (2000). May 2000, Fundamental Information Risk Management: Implementation Guide. Pages 14-37.
Information Security Forum ISF (2005a). December 2005, Improving Security Management. Enterprise-wide. Reference ISF 05-053. Pages 1-46.
Information Security Forum ISF (2005b). The Standard of Good Practice for Information Security. Reference ISF 05-104. Pages 1-28.
Information Security Forum, ISF (2005c). Information Security Health Check version 1.1. Reference ISF 05-SHC. Pages 2-8.
Information Security Forum ISF (2006). Survey Results. Reference ISF 06-0303. Pages 1-9.
Irwin-McCaughey, Elizabeth (2006). ‘Central bank risk management’. Presentation given at the 2006 Risk Management and Internal Audit specialised training course at the Federal Reserve of New York (USA), 8 May 2006.
ISO (2002). ISO Guide 73 – Risk Management – Vocabulary – Guidelines for use in Standards. Reference: ISO/IEC GUIDE 73:2002(E/F). Pages 1-16.
ISO (2004). ISO/IEC 13335-1 Information technology – Security techniques – Management of information and communications technology security. Part 1: Concepts and models for information and communications technology security management. Reference: ISO/IEC 13335-1:2004(E). Pages 1-28.
ISO (2005) ISO/IEC 17799 Information technology – Security techniques – Code of practice for information security management. Second edition 2005-06-15. Reference: ISO/IEC 17799-1:2005(E). Pages 1-115.
Kaplan, Robert S., Norton, David P. (1992). ‘The Balanced Scorecard: measures that drive performance’. Harvard Business Review. Article reprint 1 July 2005 (Product name R0507Q). Pages 1-12.
Kilian, Lutz; Manganelli, Simone (2003). ‘The central banker as a risk manager: Quantifying and forecasting inflation risks’ [online]. 15 April 2003. European Central Bank (ECB) Working Paper no. 226. Pages 1-15. Available at http://www.ecb.int/pub/pdf/scpwps/ecbwp226.pdf [Last accessed 12 May 2006].
Leippold, M. and Vanini, P. (2003). The quantification of operational risk. University of Southern Switzerland and Zürcher Kantonalbank. Pages 1-10 and 22-36. Available at http://www.gloriamundi.org/download.asp?ResourceID=453056815 [Date of access: April 17 2006]
Leskela, Lane; Knox, Mary; Schehr, David; Furlonger, David; Redshaw, Peter (2005). ‘Client issues 2005: How to achieve regulatory compliance and ERM’, Gartner, Research note. 29 March 2005. ID Number: G00126561. Pages 1-4.
Lewis, Christopher M; Lantsman, Yakov (2005). ‘What is a fair price to transfer the risk of unauthorised trading? A case study on operational risk’. Chapter 16 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 315-319 and 348-351.
May, Cliff (2002). ‘Risk Management – Practising what we preach’, Computer Fraud & Security, 8: 10-13.
McFadzean, Elspeth, Ezingeard, Jean-Noël and Birchall, David (2003). ‘Boards of Directors’ engagement with Information Security’, Henley Management College, working paper series. HWP 0309. Pages 1-25.
Mogull, R. (2004). ‘Gartner’s simple enterprise risk management framework’, Gartner, Strategic analysis report. 10 December 2004. G00125380. Pages 1-14.
Morrison, Alan D. (2005). ‘Sarbanes-Oxley, Corporate Governance and Operational Risk’. Chapter 13 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 247-271.
NIST (2002). ‘Risk management guide for information technology systems’. National Institute of Standards and Technology NIST (Technology Administration. U.S Department of Commerce). Recommendations. Special publication 800-30 by Stoneburner, Gary; Goguen, Alice and Feringa, Alexis. Pages 1-F1.
Organisation for Economic Co-operation and Development (2002). OECD Guidelines for the security of information systems and networks: towards a culture of security. Adopted as a Recommendation of the OECD Council at its 1037 Session on 25 July 2002. Pages 1-19.
Organisation for Economic Co-operation and Development (2003). Implementation plan for the OECD guidelines for the security of information systems and networks: towards a culture of security. Working Party on Information Security and Privacy. 2 July 2003. Pages 1-6.
Proctor, Paul (2005). ‘Security and Risk Compliance Overview. Security & Risk Strategies, Security Infusion’, Meta Group, Meta Practice 2339. Pages 1-7.
Rinnooy Kan, A.H.G. (2004). ‘IT governance and corporate governance at ING’. Information systems control journal. 2 26-31.
Rubin, Robert (2006). ‘An uncertain and complex global economy: outlook, opportunities and challenges’. Keynote address at the ECB Conference on Financial Globalisation and Integration. 17 July 2006.
RSA Security (2005). Trends and attitudes in Information Security – AN RSA Security e-book [online]. Pages 1-7 and 23. Available from: http://www.rsasecurity.com/go/identity/files/RSA_e-book_a5_Final.pdf
[Last accessed 9 May 2006]
Rybczynski, Tony. Podcast from Wharton titled ‘Security, Business Continuity and the 'Real-time Virtual Enterprise' interviewing Tony Rybczynski (director of strategic marketing and technologies for Nortel)[online]. Available from: http://knowledge.wharton.upenn.edu/audio/WTC_RybczynskiINT.mp3 [Last accessed 5 May 2006]
Schachter, Barry (1997). ‘An irreverent guide to value at risk’ [online]. Page 1. Available from: http://www.gloriamundi.org/introduction.asp [Last accessed 11 May 2006].
Sheffi, Yossi and Rice Jr., James B. (2005). ‘A supply chain view of the resilient enterprise’ MITSloan Management Review. Fall 2005. Vol. 47 No.1. Pages 45-47.
Scholtz, Tom (2004a). ‘Articulating the Business Value of Information Security. Security & Risk Strategies, Security Infusion, Global Networking Strategies’, Meta Group, Meta Delta 2774. Pages 1-4.
Scholtz, Tom (2004b). ‘META Group Information Security Services Framework Update: Version 3: Enterprise Planning & Architecture Strategies, Security & Risk Strategies, Security Infusion’, Meta Group, Meta Delta 3137. Pages 1-6.
Scholtz, Tom (2004c). ‘Organising for security: trends and best practices. Executive directions, security and risk strategies, security infusion’. Meta Practice. 27 July 2004. Practice 2223. Pages 1-8.
Slywotzky, Adrian J; Drzik, John (2005). ‘Countering the biggest risk of all‘. Harvard Business Review. April 2005. Pages 78-88.
Soo Hoo, Kevin J. (2000). ‘How much is enough? A risk-management approach to computer security’ Consortium for Research on Information Security and Policy (CRISP) Working paper. June 2000. Pages 1-6 and 15-20.
Straub Jr, D.W. (1990). ‘Effective IS Security: An Empirical Study’, The Institute of Management Sciences, Information Systems Research 1(3):255-276.
Straub, D. W. and R. J. Welke (1998). "Coping with systems risk: Security planning models for management decision making." MIS Quarterly 22(4): 441-469.
Tabb, Larry (2005). “Re-defining risk”. Perspectives. Wall Street & Technology September 2005. ABI/INFORM Global. Page 58.
The Economist (2006a). “The trial of Sarbanes-Oxley”. Published 22 April 2006. Pages 59-60.
The Economist (2006b). “A survey of international banking”. Published 20 May 2006. Pages 12–14.
Thompson, John with Martin, Frank (2005). Strategic management. Thomson 5th edition. Key success factors and E-V-R congruence. Pages 114 and 125-130.
Venkatraman, N. (1994). "IT-Enabled Business Transformation: From Automation to Business Scope Redefinition." Sloan Management Review 35(2): 73-87
Vinella, Peter; Jin, Jeanette (2005). ‘A Foundation for KPI and KRI’. Chapter 6 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 157-167.
Viney, Christopher (2005). ‘Model behaviour’. Chapter 9 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 201-214.
von Solms, Basie (2005a). ‘Information Security Governance: COBIT or ISO 17799 or both?’, Computers & Security 24, 99-104
von Solms, Basie (2005b). ‘Information Security Governance: Compliance management vs operational management’, Computers & Security, 24, 443-447.
von Solms, Basie (2006). ‘Information Security – The Fourth Wave’, Computers & Security, 25, 165-168.
Wikipedia. Definition of Enterprise Risk Management. Pages 1-2. Available from: http://en.wikipedia.org/wiki/Enterprise_Risk_Management [Accessed 16 December 2005]
Wright, Marie (1999). ‘Third Generation Risk Management Practices’, Computer Fraud & Security February 1999 3723/99. Pages 9-12.
Alvarez, Gene (2005). ‘An Operational Risk Management Framework’. Chapter 11 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 227-236.
Andersen, Arthur (2001). Basel and operational risk: new perspectives, new challenges. Financial services (March 2001). Pages 1-6.
Appel, Willie (2005). ‘Redefining IT Governance Readiness’, Meta Group, Meta Practice 2369. Pages 1-8.
Basel Committee on Banking Supervision. Risk Management Group. Cole, Roger (chairman) et. al. (2003). ‘Sound practices for the management and supervision of operational risk’, Bank for International Settlements (BIS). Pages 2-5 and 8.
Birchall, David, Ezingeard, Jean-Noël and McFadzean, Elspeth (2003). Information security. Setting the boardroom agenda. Grist and Henley Management College sponsored by Qinetiq. Executive summary also referenced. Pages 1-51.
Birchall, David, Ezingeard, Jean-Noël and McFadzean, Elspeth (2004). Information assurance. Strategic alignment and competitive advantage. Grist and Henley Management College sponsored by Qinetiq. Executive summary also referenced. Pages 1-73.
Bolton, Nick; Berkey, Judson (2005). ‘Aligning Basel II Operational Risk and Sarbanes-Oxley 404 Projects’. Chapter 12 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 237-246.
Booker, Robert (2006). ‘Re-engineering enterprise security’, Computers & Security 25. 13-17
Carey, Allan (2005). ‘2005 Global information security workforce study’, IDC whitepaper, sponsored by ISC2. Pages 1-28.
COBIT. IT Governance Institute (2000). ‘Control objectives for information and related technologies’ COBIT, 3rd edition. Pages 1-12.
Coles, Robert S. and Moulton, Rolf (2003). ‘Operationalizing IT risk management’,
Computers & Security 0167-4048/03. Pages 487-492.
Committee of Sponsoring Organisations of the Treadway Commission COSO (2004). Enterprise Risk Management Framework – Executive summary – Exposure Draft for Public Comment (pages 1-103) downloadable from www.coso.org/publications.htm
DeLotto, R., McKibben, D. and Leskela, L. (2003). ‘Risk management in the new regulatory environment’, Gartner, Research note 19 March 2003. COM-19-4409. Pages 1-4.
Dierick, Frank; Pires, Fatima; Scheicher, Martin; Spitzer, Kai Gereon (2005). ‘The new Basel capital framework and its implementation in the European Union’ [online]. European Central Bank (ECB) Occassional Paper Series no. 42 December 2005. Pages 1-28. Available at http://www.ecb.int/pub/pdf/scpops/ecbocp42.pdf [Last accessed 12 May 2006].
Dillon, Robin L. and Paté-Cornell, Elisabeth (2005). ‘Including technical and security risks in the management of information systems: a programmatic risk management model’. Systems engineering. 8. 1. Regular paper. Pages 15, 17, 18 and 24.
Ernst&Young (2005). Ernst & Young’s 8th annual Global Information Security Survey [online]. Pages 1-28. Available from: http://int.sitestat.com/ernst-and-young/international/s?Global-Information-Security-survey-2005&ns_type=pdf [Last accessed 8 May 2006]. Press release Available at http://www.ey.com/GLOBAL/content.nsf/International/Press_Release_-_2005_Global_Information_Security_Survey [Last accessed 8 May 2006]
Expansión (2006). “El libro abierto de Basilea II”. Published 30 June 2006. Page 20.
Ezingeard, Jean-Noël (2003). ‘Expert advice’ [online]. Available at http://www.infoconomy.com and http://www.information-age.com/article/2003/june/expert_advice . Security perspective [Last accessed 18 December 2005]. Pages 1-2.
Ezingeard, J.-N., M. Bowen-Schrire, et al. (2004). Triggers of Change in Information Security Management. ISOneWorld Conference, Las Vegas, Information Institute (http://www.information-institute.org/). Pages 1-37.
Fujii (2005). ‘Building Scenarios’. Chapter 7 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 169-178.
Giraud, Jean-Rene (2005a). ‘Managing hedge funds’ exposure to operational risks’. Chapter 14 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 275-283.
Giraud, Jean-Rene (2005b). ‘Managing hedge funds’ operational risks’. Chapter 14 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 284-294.
Giraud, Jean-Rene (2005c). ‘Quantifying hedge funds’ operational risks’. Chapter 14 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 295-303.
Hamel, Gary (2006). ‘The Why, What and How of Management Innovation’. Harvard Business Review. February 2006. Pages 1-12.
Hughes, Peter (2005). ‘Using transactional data to measure operational risk’. Chapter 1 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 3-12.
Huijgens, Hennie (2004). ‘Value chain control – An IT control approach that puts business in the centre’. Information systems control journal. 2 57-62.
Information Security Forum ISF (2000). May 2000, Fundamental Information Risk Management: Implementation Guide. Pages 14-37.
Information Security Forum ISF (2005a). December 2005, Improving Security Management. Enterprise-wide. Reference ISF 05-053. Pages 1-46.
Information Security Forum ISF (2005b). The Standard of Good Practice for Information Security. Reference ISF 05-104. Pages 1-28.
Information Security Forum, ISF (2005c). Information Security Health Check version 1.1. Reference ISF 05-SHC. Pages 2-8.
Information Security Forum ISF (2006). Survey Results. Reference ISF 06-0303. Pages 1-9.
Irwin-McCaughey, Elizabeth (2006). ‘Central bank risk management’. Presentation given at the 2006 Risk Management and Internal Audit specialised training course at the Federal Reserve of New York (USA), 8 May 2006.
ISO (2002). ISO Guide 73 – Risk Management – Vocabulary – Guidelines for use in Standards. Reference: ISO/IEC GUIDE 73:2002(E/F). Pages 1-16.
ISO (2004). ISO/IEC 13335-1 Information technology – Security techniques – Management of information and communications technology security. Part 1: Concepts and models for information and communications technology security management. Reference: ISO/IEC 13335-1:2004(E). Pages 1-28.
ISO (2005) ISO/IEC 17799 Information technology – Security techniques – Code of practice for information security management. Second edition 2005-06-15. Reference: ISO/IEC 17799-1:2005(E). Pages 1-115.
Kaplan, Robert S., Norton, David P. (1992). ‘The Balanced Scorecard: measures that drive performance’. Harvard Business Review. Article reprint 1 July 2005 (Product name R0507Q). Pages 1-12.
Kilian, Lutz; Manganelli, Simone (2003). ‘The central banker as a risk manager: Quantifying and forecasting inflation risks’ [online]. 15 April 2003. European Central Bank (ECB) Working Paper no. 226. Pages 1-15. Available at http://www.ecb.int/pub/pdf/scpwps/ecbwp226.pdf [Last accessed 12 May 2006].
Leippold, M. and Vanini, P. (2003). The quantification of operational risk. University of Southern Switzerland and Zürcher Kantonalbank. Pages 1-10 and 22-36. Available at http://www.gloriamundi.org/download.asp?ResourceID=453056815 [Date of access: April 17 2006]
Leskela, Lane; Knox, Mary; Schehr, David; Furlonger, David; Redshaw, Peter (2005). ‘Client issues 2005: How to achieve regulatory compliance and ERM’, Gartner, Research note. 29 March 2005. ID Number: G00126561. Pages 1-4.
Lewis, Christopher M; Lantsman, Yakov (2005). ‘What is a fair price to transfer the risk of unauthorised trading? A case study on operational risk’. Chapter 16 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 315-319 and 348-351.
May, Cliff (2002). ‘Risk Management – Practising what we preach’, Computer Fraud & Security, 8: 10-13.
McFadzean, Elspeth, Ezingeard, Jean-Noël and Birchall, David (2003). ‘Boards of Directors’ engagement with Information Security’, Henley Management College, working paper series. HWP 0309. Pages 1-25.
Mogull, R. (2004). ‘Gartner’s simple enterprise risk management framework’, Gartner, Strategic analysis report. 10 December 2004. G00125380. Pages 1-14.
Morrison, Alan D. (2005). ‘Sarbanes-Oxley, Corporate Governance and Operational Risk’. Chapter 13 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 247-271.
NIST (2002). ‘Risk management guide for information technology systems’. National Institute of Standards and Technology NIST (Technology Administration. U.S Department of Commerce). Recommendations. Special publication 800-30 by Stoneburner, Gary; Goguen, Alice and Feringa, Alexis. Pages 1-F1.
Organisation for Economic Co-operation and Development (2002). OECD Guidelines for the security of information systems and networks: towards a culture of security. Adopted as a Recommendation of the OECD Council at its 1037 Session on 25 July 2002. Pages 1-19.
Organisation for Economic Co-operation and Development (2003). Implementation plan for the OECD guidelines for the security of information systems and networks: towards a culture of security. Working Party on Information Security and Privacy. 2 July 2003. Pages 1-6.
Proctor, Paul (2005). ‘Security and Risk Compliance Overview. Security & Risk Strategies, Security Infusion’, Meta Group, Meta Practice 2339. Pages 1-7.
Rinnooy Kan, A.H.G. (2004). ‘IT governance and corporate governance at ING’. Information systems control journal. 2 26-31.
Rubin, Robert (2006). ‘An uncertain and complex global economy: outlook, opportunities and challenges’. Keynote address at the ECB Conference on Financial Globalisation and Integration. 17 July 2006.
RSA Security (2005). Trends and attitudes in Information Security – AN RSA Security e-book [online]. Pages 1-7 and 23. Available from: http://www.rsasecurity.com/go/identity/files/RSA_e-book_a5_Final.pdf
[Last accessed 9 May 2006]
Rybczynski, Tony. Podcast from Wharton titled ‘Security, Business Continuity and the 'Real-time Virtual Enterprise' interviewing Tony Rybczynski (director of strategic marketing and technologies for Nortel)[online]. Available from: http://knowledge.wharton.upenn.edu/audio/WTC_RybczynskiINT.mp3 [Last accessed 5 May 2006]
Schachter, Barry (1997). ‘An irreverent guide to value at risk’ [online]. Page 1. Available from: http://www.gloriamundi.org/introduction.asp [Last accessed 11 May 2006].
Sheffi, Yossi and Rice Jr., James B. (2005). ‘A supply chain view of the resilient enterprise’ MITSloan Management Review. Fall 2005. Vol. 47 No.1. Pages 45-47.
Scholtz, Tom (2004a). ‘Articulating the Business Value of Information Security. Security & Risk Strategies, Security Infusion, Global Networking Strategies’, Meta Group, Meta Delta 2774. Pages 1-4.
Scholtz, Tom (2004b). ‘META Group Information Security Services Framework Update: Version 3: Enterprise Planning & Architecture Strategies, Security & Risk Strategies, Security Infusion’, Meta Group, Meta Delta 3137. Pages 1-6.
Scholtz, Tom (2004c). ‘Organising for security: trends and best practices. Executive directions, security and risk strategies, security infusion’. Meta Practice. 27 July 2004. Practice 2223. Pages 1-8.
Slywotzky, Adrian J; Drzik, John (2005). ‘Countering the biggest risk of all‘. Harvard Business Review. April 2005. Pages 78-88.
Soo Hoo, Kevin J. (2000). ‘How much is enough? A risk-management approach to computer security’ Consortium for Research on Information Security and Policy (CRISP) Working paper. June 2000. Pages 1-6 and 15-20.
Straub Jr, D.W. (1990). ‘Effective IS Security: An Empirical Study’, The Institute of Management Sciences, Information Systems Research 1(3):255-276.
Straub, D. W. and R. J. Welke (1998). "Coping with systems risk: Security planning models for management decision making." MIS Quarterly 22(4): 441-469.
Tabb, Larry (2005). “Re-defining risk”. Perspectives. Wall Street & Technology September 2005. ABI/INFORM Global. Page 58.
The Economist (2006a). “The trial of Sarbanes-Oxley”. Published 22 April 2006. Pages 59-60.
The Economist (2006b). “A survey of international banking”. Published 20 May 2006. Pages 12–14.
Thompson, John with Martin, Frank (2005). Strategic management. Thomson 5th edition. Key success factors and E-V-R congruence. Pages 114 and 125-130.
Venkatraman, N. (1994). "IT-Enabled Business Transformation: From Automation to Business Scope Redefinition." Sloan Management Review 35(2): 73-87
Vinella, Peter; Jin, Jeanette (2005). ‘A Foundation for KPI and KRI’. Chapter 6 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 157-167.
Viney, Christopher (2005). ‘Model behaviour’. Chapter 9 of the book titled ‘Operational Risk: Practical approaches to implementation’. Edited by Ellen Davis. Risk books. Pages 201-214.
von Solms, Basie (2005a). ‘Information Security Governance: COBIT or ISO 17799 or both?’, Computers & Security 24, 99-104
von Solms, Basie (2005b). ‘Information Security Governance: Compliance management vs operational management’, Computers & Security, 24, 443-447.
von Solms, Basie (2006). ‘Information Security – The Fourth Wave’, Computers & Security, 25, 165-168.
Wikipedia. Definition of Enterprise Risk Management. Pages 1-2. Available from: http://en.wikipedia.org/wiki/Enterprise_Risk_Management [Accessed 16 December 2005]
Wright, Marie (1999). ‘Third Generation Risk Management Practices’, Computer Fraud & Security February 1999 3723/99. Pages 9-12.
Literature review: Summary
The reviewed literature has shown the need to align activities, including risk management, with the strategy and objectives of the organisation.
It has gone in depth into risk and risk management. It has introduced the concept of holistic or enterprise risk management together with the motivating role of compliance, which is in opposition to current silo mentality in risk management.
Subsequently, it has identified the twofold role of information as risk connector of different risks and business process element and what organisations need to do to practise an effective information security, contrasting it with how it is currently done in organisations.
This review has also presented the pervasive nature of operational risks in organisations and finally, it has provided references on reasons to link these risk management practices and on how to do so and the benefits this tie provides to the organisation.
The final part of this review deals with an indispensable condition for this link to succeed and bring real benefits to the organisation: management commitment. This condition falls under management innovation.
It has gone in depth into risk and risk management. It has introduced the concept of holistic or enterprise risk management together with the motivating role of compliance, which is in opposition to current silo mentality in risk management.
Subsequently, it has identified the twofold role of information as risk connector of different risks and business process element and what organisations need to do to practise an effective information security, contrasting it with how it is currently done in organisations.
This review has also presented the pervasive nature of operational risks in organisations and finally, it has provided references on reasons to link these risk management practices and on how to do so and the benefits this tie provides to the organisation.
The final part of this review deals with an indispensable condition for this link to succeed and bring real benefits to the organisation: management commitment. This condition falls under management innovation.
In a nutshell
Answer to the research question
The research question is how companies can link systematically their information security practice with their operational risk management strategy and practice to achieve superior benefits.
The answer, based on the reviewed literature, would be that the three necessary elements for organisations to obtain superior benefits are:
• The presence of a committed management (setting risk objectives and appetite). Reviewed literature and survey results show that this is the first necessary requirement.
• The development of a strong information security practice as part of a holistic ERM/ORM.
• The alignment of enterprise risk management with the business strategy. This study explains that making business is taking risks and survey results show the relation between strategic alignment in RM and benefits for the organisation.
Stakeholder value, new business opportunities and better governance are currently the most likely superior benefits to achieve according to surveyed experts.
Therefore, as Jean Noel Ezingeard states, "an integrated operational risk management approach seems to be the cornerstone of success and will deliver beyond the risk management functions".
The research question is how companies can link systematically their information security practice with their operational risk management strategy and practice to achieve superior benefits.
The answer, based on the reviewed literature, would be that the three necessary elements for organisations to obtain superior benefits are:
• The presence of a committed management (setting risk objectives and appetite). Reviewed literature and survey results show that this is the first necessary requirement.
• The development of a strong information security practice as part of a holistic ERM/ORM.
• The alignment of enterprise risk management with the business strategy. This study explains that making business is taking risks and survey results show the relation between strategic alignment in RM and benefits for the organisation.
Stakeholder value, new business opportunities and better governance are currently the most likely superior benefits to achieve according to surveyed experts.
Therefore, as Jean Noel Ezingeard states, "an integrated operational risk management approach seems to be the cornerstone of success and will deliver beyond the risk management functions".
Present and future
The creation of this blog has two objectives:
Firstly, providing respondents answering the survey with an overview of the extension and results of the study.
And secondly, creating a discussion forum where readers and authors can further develop these topics.
Please feel free to leave a comment in this blog or just to contact me (apartidar at yahoo dot com) in case you would like:
- further details of the study carried out until today
- any other suggestion/question/project you could share with the infosec/risk management community or with the authors of this blog
- to find peer review possibilities on this topics
The information risk management adventure has only just started...
Firstly, providing respondents answering the survey with an overview of the extension and results of the study.
And secondly, creating a discussion forum where readers and authors can further develop these topics.
Please feel free to leave a comment in this blog or just to contact me (apartidar at yahoo dot com) in case you would like:
- further details of the study carried out until today
- any other suggestion/question/project you could share with the infosec/risk management community or with the authors of this blog
- to find peer review possibilities on this topics
The information risk management adventure has only just started...
Annex: Link to the survey
Information security and operational risk.
How do companies face and manage risks currently? Do their diverse risk management functions still work in silos? Where does information security fit in this risk management puzzle? Among others, these questions are the triggers for an academic information security study that I am carrying out.
The study investigates how the link of information security with operational risk management brings benefits to any organisation. The financial sector is a clear example for this, where strong regulatory drivers push for an integrated enterprise risk management.
A key quantitative data collection tool for this study is an anonymous survey available at http://securityandrisk.aedranet.com .
The survey requires only some minutes. Before the end of 2006, all participants providing an e-mail address will receive an executive summary with the main results of the study. No link will exist between the given email address and the answers.
How do companies face and manage risks currently? Do their diverse risk management functions still work in silos? Where does information security fit in this risk management puzzle? Among others, these questions are the triggers for an academic information security study that I am carrying out.
The study investigates how the link of information security with operational risk management brings benefits to any organisation. The financial sector is a clear example for this, where strong regulatory drivers push for an integrated enterprise risk management.
A key quantitative data collection tool for this study is an anonymous survey available at http://securityandrisk.aedranet.com .
The survey requires only some minutes. Before the end of 2006, all participants providing an e-mail address will receive an executive summary with the main results of the study. No link will exist between the given email address and the answers.
Annex: Survey questions
These were the questions present in the survey
Information security and operational risk
Welcome to this information security study.
This survey contains 6 initial questions and 38 statements. All answers remain anonymous.
Please answer the questions and indicate your level of agreement with the statements.
At the end of the survey, you can provide an email address where you will receive an executive summary of the results of this study. No link will exist between the email address and the answers.
Thank you for your contribution.
Let's first start with six questions.
Question 1. What is the name of your current position?
Choose only one of the following
Chief Risk Management Officer
Risk Management Expert
Chief Information Security Officer
Information Security Expert
Chief Information Systems Security Officer (CISSO)
Information Systems Security Expert
Other
Question 2. How long have you been working in your current position?
Less than 1 year
Between 1 and 3 years
Between 3 and 5 years
More than 5 years
Question 3. In which field of expertise was your previous position located?
Choose only one of the following
Risk Management
Information Technology
Audit
Other
Question 4. Which position do you report to?
Choose only one of the following
The Chief Information Systems Officer
The Chief Financial Officer
The Chief Internal Audit Officer
The Chief Executive Officer
The Executive Board
Other
Question 5. How many employees are influenced (directly or indirectly) by the work your group does?
Less than 100
Between 100 and 1000
Between 1001 and 10000
Between 10001 and 100000
More than 100000
Question 6. In which sector does your organisation operate?
Choose only one of the following
Telecommunications
Administration
Financial sector
Utilities
Other
Thank you for answering these 6 questions. There are now 38 statements to disagree or agree with.
Statement 1. My organisation currently uses information technology (IT) to transform its business processes.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 2. My organisation considers that global risk management is a strategic activity that requires all employees' involvement.
1 2 3 4 5
Please select only one answer per statement. All statements follow the same scale. Possible answers range from strong disagreement (1) to strong agreement (5).
Statement 3. In my organisation, changes to business processes happen frequently.
1 2 3 4 5
Statement 4. In my organisation, changes to management structures happen frequently.
1 2 3 4 5
Statement 5. My organisation is ready to practice transparency in its corporate governance by being open to stakeholders about its risk exposure.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 6. My organisation's management sets long term (e.g. 2 years) information security objectives.
1 2 3 4 5
Statement 7. My organisation's management sets middle term (e.g. 6 months) information security objectives.
1 2 3 4 5
Statement 8. My organisation's management shows a high level of commitment to information security.
1 2 3 4 5
Statement 9. My organisation performs information risk analysis based on business impact assessments.
1 2 3 4 5
Statement 10. My organisation performs information risk analysis based on threat and vulnerability analysis.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 11. The information owner always receives the results of the risk analysis.
1 2 3 4 5
Statement 12. The information owner is responsible for accepting or mitigating risks.
1 2 3 4 5
Statement 13. My organisation has a security policy approved by management.
1 2 3 4 5
Statement 14. The security policy has been actively communicated to all employees.
1 2 3 4 5
Statement 15. In my organisation, an executive committee is accountable for information security.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 16. In my organisation, an executive committee is accountable for the implementation of information security controls.
1 2 3 4 5
Statement 17. In my organisation, an executive committee is accountable for operational risk.
1 2 3 4 5
Statement 18. In my organisation, an executive committee is accountable for the implementation of an operational risk management model.
1 2 3 4 5
Statement 19. In my organisation, the information security function collaborates with the information systems security function.
1 2 3 4 5
Statement 20. In my organisation, management has provided a clear message about which risks can be accepted and which risks can't.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 21. In my organisation, the message about acceptable risks is documented.
1 2 3 4 5
Statement 22. In my organisation, the message about acceptable risks is accessible
by all employees.
1 2 3 4 5
Statement 23. In my organisation, the current information security practice helps comply with regulatory requirements.
1 2 3 4 5
Statement 24. In my organisation, the current information security practice influences positively my organisation's operations.
1 2 3 4 5
Statement 25. In my organisation, the current information security practice facilitates new business opportunities.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 26. In my organisation, the current information security practice increases the degree of loyalty shown by partner organisations and customers.
1 2 3 4 5
Statement 27. In my organisation, the current information security practice contributes to its corporate governance.
1 2 3 4 5
Statement 28. In my organisation, the current information security practice improves its financing capability.
1 2 3 4 5
Statement 29. In my organisation, the current information security practice helps increase sales.
1 2 3 4 5
Statement 30. In my organisation, the current information security practice helps save costs.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 31. My organisation's risk management strategy is aligned with its business strategy.
1 2 3 4 5
Statement 32. My organisation's information security strategy is aligned with its business strategy.
1 2 3 4 5
Statement 33. My organisation's information systems security strategy is aligned with its business strategy.
1 2 3 4 5
Statement 34. My organisation's risk management practice provides a competitive advantage to my organisation.
1 2 3 4 5
Statement 35. My organisation's information security practice provides a competitive advantage to my organisation.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 36. My organisation's risk management practice provides a greater value to its stakeholders.
1 2 3 4 5
Statement 37. My organisation's information security practice provides a greater value to its stakeholders.
1 2 3 4 5
Statement 38. In my organisation, risks will be managed in a more coordinated way.
1 2 3 4 5
Thank you very much for your answers. They are very valuable for this study. If you wish to receive an executive summary before the end of 2006, please insert an email address to receive it. No link will exist between the email address and your answers.
Information security and operational risk
Welcome to this information security study.
This survey contains 6 initial questions and 38 statements. All answers remain anonymous.
Please answer the questions and indicate your level of agreement with the statements.
At the end of the survey, you can provide an email address where you will receive an executive summary of the results of this study. No link will exist between the email address and the answers.
Thank you for your contribution.
Let's first start with six questions.
Question 1. What is the name of your current position?
Choose only one of the following
Chief Risk Management Officer
Risk Management Expert
Chief Information Security Officer
Information Security Expert
Chief Information Systems Security Officer (CISSO)
Information Systems Security Expert
Other
Question 2. How long have you been working in your current position?
Less than 1 year
Between 1 and 3 years
Between 3 and 5 years
More than 5 years
Question 3. In which field of expertise was your previous position located?
Choose only one of the following
Risk Management
Information Technology
Audit
Other
Question 4. Which position do you report to?
Choose only one of the following
The Chief Information Systems Officer
The Chief Financial Officer
The Chief Internal Audit Officer
The Chief Executive Officer
The Executive Board
Other
Question 5. How many employees are influenced (directly or indirectly) by the work your group does?
Less than 100
Between 100 and 1000
Between 1001 and 10000
Between 10001 and 100000
More than 100000
Question 6. In which sector does your organisation operate?
Choose only one of the following
Telecommunications
Administration
Financial sector
Utilities
Other
Thank you for answering these 6 questions. There are now 38 statements to disagree or agree with.
Statement 1. My organisation currently uses information technology (IT) to transform its business processes.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 2. My organisation considers that global risk management is a strategic activity that requires all employees' involvement.
1 2 3 4 5
Please select only one answer per statement. All statements follow the same scale. Possible answers range from strong disagreement (1) to strong agreement (5).
Statement 3. In my organisation, changes to business processes happen frequently.
1 2 3 4 5
Statement 4. In my organisation, changes to management structures happen frequently.
1 2 3 4 5
Statement 5. My organisation is ready to practice transparency in its corporate governance by being open to stakeholders about its risk exposure.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 6. My organisation's management sets long term (e.g. 2 years) information security objectives.
1 2 3 4 5
Statement 7. My organisation's management sets middle term (e.g. 6 months) information security objectives.
1 2 3 4 5
Statement 8. My organisation's management shows a high level of commitment to information security.
1 2 3 4 5
Statement 9. My organisation performs information risk analysis based on business impact assessments.
1 2 3 4 5
Statement 10. My organisation performs information risk analysis based on threat and vulnerability analysis.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 11. The information owner always receives the results of the risk analysis.
1 2 3 4 5
Statement 12. The information owner is responsible for accepting or mitigating risks.
1 2 3 4 5
Statement 13. My organisation has a security policy approved by management.
1 2 3 4 5
Statement 14. The security policy has been actively communicated to all employees.
1 2 3 4 5
Statement 15. In my organisation, an executive committee is accountable for information security.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 16. In my organisation, an executive committee is accountable for the implementation of information security controls.
1 2 3 4 5
Statement 17. In my organisation, an executive committee is accountable for operational risk.
1 2 3 4 5
Statement 18. In my organisation, an executive committee is accountable for the implementation of an operational risk management model.
1 2 3 4 5
Statement 19. In my organisation, the information security function collaborates with the information systems security function.
1 2 3 4 5
Statement 20. In my organisation, management has provided a clear message about which risks can be accepted and which risks can't.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 21. In my organisation, the message about acceptable risks is documented.
1 2 3 4 5
Statement 22. In my organisation, the message about acceptable risks is accessible
by all employees.
1 2 3 4 5
Statement 23. In my organisation, the current information security practice helps comply with regulatory requirements.
1 2 3 4 5
Statement 24. In my organisation, the current information security practice influences positively my organisation's operations.
1 2 3 4 5
Statement 25. In my organisation, the current information security practice facilitates new business opportunities.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 26. In my organisation, the current information security practice increases the degree of loyalty shown by partner organisations and customers.
1 2 3 4 5
Statement 27. In my organisation, the current information security practice contributes to its corporate governance.
1 2 3 4 5
Statement 28. In my organisation, the current information security practice improves its financing capability.
1 2 3 4 5
Statement 29. In my organisation, the current information security practice helps increase sales.
1 2 3 4 5
Statement 30. In my organisation, the current information security practice helps save costs.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 31. My organisation's risk management strategy is aligned with its business strategy.
1 2 3 4 5
Statement 32. My organisation's information security strategy is aligned with its business strategy.
1 2 3 4 5
Statement 33. My organisation's information systems security strategy is aligned with its business strategy.
1 2 3 4 5
Statement 34. My organisation's risk management practice provides a competitive advantage to my organisation.
1 2 3 4 5
Statement 35. My organisation's information security practice provides a competitive advantage to my organisation.
1 = I strongly disagree with this statement
2 = I disagree with this statement
3 = I neither disagree nor agree with this statement
4 = I agree with this statement
5 = I strongly agree with this statement
Please select only one answer per statement. All statements follow the same scale.
Statement 36. My organisation's risk management practice provides a greater value to its stakeholders.
1 2 3 4 5
Statement 37. My organisation's information security practice provides a greater value to its stakeholders.
1 2 3 4 5
Statement 38. In my organisation, risks will be managed in a more coordinated way.
1 2 3 4 5
Thank you very much for your answers. They are very valuable for this study. If you wish to receive an executive summary before the end of 2006, please insert an email address to receive it. No link will exist between the email address and your answers.
Annex: Survey questions (Spanish)
Seguridad de la información y riesgo operacional.
Bienvenido a este estudio de seguridad de la información.
Este cuestionario consta de 6 preguntas iniciales y 38 afirmaciones. Todas las respuestas son anónimas.
Por favor conteste las preguntas iniciales e indique si está o no de acuerdo con las afirmaciones.
Al final del cuestionario, puede introducir una dirección de correo donde podrá recibir un resumen de los resultados de este estudio. Las respuestas al cuestionario no se asocian con la dirección de correo proporcionada.
Gracias por su participación.
Estas son las 6 preguntas iniciales:
Pregunta 1. ¿Cuál es el nombre de su actual puesto?
Elija solamente uno del siguiente
Responsable de gestión de riesgos
Experto en gestión de riesgos
Responsable de seguridad de la información
Experto en seguridad de la información
Responsable de seguridad en sistemas de información
Experto en seguridad en sistemas de información
Otro
Pregunta 2. ¿Cuánto tiempo lleva trabajando en su puesto actual?
Menos de 1 año
Entre 1 y 3 años
Entre 3 y 5 años
Más de 5 años
Pregunta 3. ¿Dentro de qué especialidad se encontraba su anterior puesto?
Elija solamente uno del siguiente
Gestíon de riesgo
Tecnologías de la información
Auditoría
Otro
Pregunta 4. ¿De qué cargo depende su puesto?
Elija solamente uno del siguiente
Del responsable de sistemas de información
Del responsable financiero
Del responsable de auditoría interna
Del máximo responsable ejecutivo (consejero ejecutivo, presidente)
Del consejo ejecutivo
Otro
Pregunta 5. ¿A cuántos empleados influye (directa o indirectamente) el trabajo que hace su grupo?
Menos de 100
Entre 100 y 1000
Entre 1001 y 10000
Entre 10001 y 100000
Más de 100000
Pregunta 6. ¿En qué sector trabaja su compañía?
Elija solamente uno del siguiente
Telecomunicaciones
Administración
Sector financiero
Energía
Otro
Gracias por contestar a estas 6 preguntas. A continuación hay 38 afirmaciones. Por favor indique si está o no de acuerdo con ellas.
Afirmación 1. En la actualidad, mi compañía utiliza la tecnología de la información (TTII) para transformar sus procesos de negocio.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 2. Mi compañía considera que la gestión global del riesgo es una actividad estratégica que requiere la participación de todos los empleados.
1 2 3 4 5
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala. Las respuestas posibles varían desde un total desacuerdo (1) hasta un total acuerdo (5).
Afirmación 3. En mi compañía , los cambios en los procesos de negocio suceden frecuentemente.
1 2 3 4 5
Afirmación 4. En mi compañía, los cambios en la estructura de dirección suceden frecuentemente.
1 2 3 4 5
Afirmación 5. Mi compañía está preparada para practicar la transparencia en su gobierno corporativo compartiendo su situación de riesgo con todos los grupos interesados en ella (sus stakeholders).
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 6. La dirección de mi compañía establece objetivos a largo plazo (p.e. 2 años) en seguridad de la información.
1 2 3 4 5
Afirmación 7. La dirección de mi compañía establece objetivos a medio plazo (p.e. 6 meses) en seguridad de la información.
1 2 3 4 5
Afirmación 8. La dirección de mi compañía muestra un alto nivel de compromiso con la seguridad de la información.
1 2 3 4 5
Afirmación 9. Mi compañía realiza análisis de riesgos de la información evaluando el impacto para el proceso de negocio.
1 2 3 4 5
Afirmación 10. Mi compañía realiza análisis de riesgos de la información evaluando amenazas y vulnerabilidades.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 11. El propietario de la información siempre recibe los resultados del análisis de riesgos.
1 2 3 4 5
Afirmación 12. El propietario de la información es responsable de aceptar o mitigar los riesgos.
1 2 3 4 5
Afirmación 13. Mi compañía tiene una política de seguridad aprobada por la dirección.
1 2 3 4 5
Afirmación 14. La política de seguridad ha sido comunicada activamente a todos los empleados.
1 2 3 4 5
Afirmación 15. En mi compañía, un comité ejecutivo es responsable de la seguridad de la información.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 16. En mi compañía, un comité ejecutivo es responsable de la implementación de los controles de seguridad de la información.
1 2 3 4 5
Afirmación 17. En mi compañía, un comité ejecutivo es responsable del riesgo operacional.
1 2 3 4 5
Afirmación 18. En mi compañía, un comité ejecutivo es responsable de la implementación de un modelo de gestión de riesgo operacional.
1 2 3 4 5
Afirmación 19. En mi compañía, la función de seguridad de la información colabora con la función de seguridad en sistemas de información.
1 2 3 4 5
Afirmación 20. La dirección de mi compañía ha emitido un mensaje nítido sobre cuáles son los riesgos que se pueden aceptar y cuáles no.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 21. En mi compañía, este mensaje sobre qué riesgos se pueden aceptar está documentado.
1 2 3 4 5
Afirmación 22. En mi compañía, este mensaje sobre los riesgos que se pueden aceptar es accessible a todos los empleados.
1 2 3 4 5
Afirmación 23. La práctica actual de seguridad de la información en mi compañía contribuye al cumplimiento de requisitos legales y normativos.
1 2 3 4 5
Afirmación 24. La práctica actual de seguridad de la información en mi compañía facilita sus operaciones.
1 2 3 4 5
Afirmación 25. La práctica actual de seguridad de la información en mi compañía proporciona nuevas oportunidades de negocio.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 26. La práctica actual de seguridad de la información en mi compañía aumenta el grado de fidelidad demostrado por organizaciones asociadas y clientes.
1 2 3 4 5
Afirmación 27. La práctica actual de seguridad de la información en mi compañía contribuye a su gobierno corporativo.
1 2 3 4 5
Afirmación 28. La práctica actual de seguridad de la información en mi compañía facilita su capacidad de financiación.
1 2 3 4 5
Afirmación 29. La práctica actual de seguridad de la información en mi compañía contribuye a aumentar las ventas.
1 2 3 4 5
Afirmación 30. La práctica actual de seguridad de la información en mi compañía ayuda a ahorrar costes.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 31. La estrategia de gestión de riesgos de mi compañía está alineada con su estrategia de negocio.
1 2 3 4 5
Afirmación 32. La estrategia de gestión de seguridad de la información de mi compañía está alineada con su estrategia de negocio.
1 2 3 4 5
Afirmación 33. La estrategia de gestión de seguridad en sistemas de información de mi compañía está alineada con su estrategia de negocio.
1 2 3 4 5
Afirmación 34. La gestión de riesgos de mi compañía proporciona una ventaja competitiva.
1 2 3 4 5
Afirmación 35. La seguridad de la información de mi compañía proporciona una ventaja competitiva.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 36. La gestión de riesgos de mi compañía proporciona valor a todos sus grupos de interés (sus stakeholders).
1 2 3 4 5
Afirmación 37.La seguridad de la información de mi compañía proporciona valor a todos sus grupos de interés (sus stakeholders).
1 2 3 4 5
Afirmación 38. En mi compañía, los riesgos se gestionarán de una forma más coordinada.
1 2 3 4 5
Muchas gracias por sus respuestas. Son de gran valor para este estudio. Si desea recibir un resumen del resultado de este estudio antes del final de 2006, por favor introduzca una dirección de correo electrónico. Las respuestas al cuestionario no se asocian con la dirección de correo proporcionada.
Bienvenido a este estudio de seguridad de la información.
Este cuestionario consta de 6 preguntas iniciales y 38 afirmaciones. Todas las respuestas son anónimas.
Por favor conteste las preguntas iniciales e indique si está o no de acuerdo con las afirmaciones.
Al final del cuestionario, puede introducir una dirección de correo donde podrá recibir un resumen de los resultados de este estudio. Las respuestas al cuestionario no se asocian con la dirección de correo proporcionada.
Gracias por su participación.
Estas son las 6 preguntas iniciales:
Pregunta 1. ¿Cuál es el nombre de su actual puesto?
Elija solamente uno del siguiente
Responsable de gestión de riesgos
Experto en gestión de riesgos
Responsable de seguridad de la información
Experto en seguridad de la información
Responsable de seguridad en sistemas de información
Experto en seguridad en sistemas de información
Otro
Pregunta 2. ¿Cuánto tiempo lleva trabajando en su puesto actual?
Menos de 1 año
Entre 1 y 3 años
Entre 3 y 5 años
Más de 5 años
Pregunta 3. ¿Dentro de qué especialidad se encontraba su anterior puesto?
Elija solamente uno del siguiente
Gestíon de riesgo
Tecnologías de la información
Auditoría
Otro
Pregunta 4. ¿De qué cargo depende su puesto?
Elija solamente uno del siguiente
Del responsable de sistemas de información
Del responsable financiero
Del responsable de auditoría interna
Del máximo responsable ejecutivo (consejero ejecutivo, presidente)
Del consejo ejecutivo
Otro
Pregunta 5. ¿A cuántos empleados influye (directa o indirectamente) el trabajo que hace su grupo?
Menos de 100
Entre 100 y 1000
Entre 1001 y 10000
Entre 10001 y 100000
Más de 100000
Pregunta 6. ¿En qué sector trabaja su compañía?
Elija solamente uno del siguiente
Telecomunicaciones
Administración
Sector financiero
Energía
Otro
Gracias por contestar a estas 6 preguntas. A continuación hay 38 afirmaciones. Por favor indique si está o no de acuerdo con ellas.
Afirmación 1. En la actualidad, mi compañía utiliza la tecnología de la información (TTII) para transformar sus procesos de negocio.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 2. Mi compañía considera que la gestión global del riesgo es una actividad estratégica que requiere la participación de todos los empleados.
1 2 3 4 5
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala. Las respuestas posibles varían desde un total desacuerdo (1) hasta un total acuerdo (5).
Afirmación 3. En mi compañía , los cambios en los procesos de negocio suceden frecuentemente.
1 2 3 4 5
Afirmación 4. En mi compañía, los cambios en la estructura de dirección suceden frecuentemente.
1 2 3 4 5
Afirmación 5. Mi compañía está preparada para practicar la transparencia en su gobierno corporativo compartiendo su situación de riesgo con todos los grupos interesados en ella (sus stakeholders).
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 6. La dirección de mi compañía establece objetivos a largo plazo (p.e. 2 años) en seguridad de la información.
1 2 3 4 5
Afirmación 7. La dirección de mi compañía establece objetivos a medio plazo (p.e. 6 meses) en seguridad de la información.
1 2 3 4 5
Afirmación 8. La dirección de mi compañía muestra un alto nivel de compromiso con la seguridad de la información.
1 2 3 4 5
Afirmación 9. Mi compañía realiza análisis de riesgos de la información evaluando el impacto para el proceso de negocio.
1 2 3 4 5
Afirmación 10. Mi compañía realiza análisis de riesgos de la información evaluando amenazas y vulnerabilidades.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 11. El propietario de la información siempre recibe los resultados del análisis de riesgos.
1 2 3 4 5
Afirmación 12. El propietario de la información es responsable de aceptar o mitigar los riesgos.
1 2 3 4 5
Afirmación 13. Mi compañía tiene una política de seguridad aprobada por la dirección.
1 2 3 4 5
Afirmación 14. La política de seguridad ha sido comunicada activamente a todos los empleados.
1 2 3 4 5
Afirmación 15. En mi compañía, un comité ejecutivo es responsable de la seguridad de la información.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 16. En mi compañía, un comité ejecutivo es responsable de la implementación de los controles de seguridad de la información.
1 2 3 4 5
Afirmación 17. En mi compañía, un comité ejecutivo es responsable del riesgo operacional.
1 2 3 4 5
Afirmación 18. En mi compañía, un comité ejecutivo es responsable de la implementación de un modelo de gestión de riesgo operacional.
1 2 3 4 5
Afirmación 19. En mi compañía, la función de seguridad de la información colabora con la función de seguridad en sistemas de información.
1 2 3 4 5
Afirmación 20. La dirección de mi compañía ha emitido un mensaje nítido sobre cuáles son los riesgos que se pueden aceptar y cuáles no.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 21. En mi compañía, este mensaje sobre qué riesgos se pueden aceptar está documentado.
1 2 3 4 5
Afirmación 22. En mi compañía, este mensaje sobre los riesgos que se pueden aceptar es accessible a todos los empleados.
1 2 3 4 5
Afirmación 23. La práctica actual de seguridad de la información en mi compañía contribuye al cumplimiento de requisitos legales y normativos.
1 2 3 4 5
Afirmación 24. La práctica actual de seguridad de la información en mi compañía facilita sus operaciones.
1 2 3 4 5
Afirmación 25. La práctica actual de seguridad de la información en mi compañía proporciona nuevas oportunidades de negocio.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 26. La práctica actual de seguridad de la información en mi compañía aumenta el grado de fidelidad demostrado por organizaciones asociadas y clientes.
1 2 3 4 5
Afirmación 27. La práctica actual de seguridad de la información en mi compañía contribuye a su gobierno corporativo.
1 2 3 4 5
Afirmación 28. La práctica actual de seguridad de la información en mi compañía facilita su capacidad de financiación.
1 2 3 4 5
Afirmación 29. La práctica actual de seguridad de la información en mi compañía contribuye a aumentar las ventas.
1 2 3 4 5
Afirmación 30. La práctica actual de seguridad de la información en mi compañía ayuda a ahorrar costes.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 31. La estrategia de gestión de riesgos de mi compañía está alineada con su estrategia de negocio.
1 2 3 4 5
Afirmación 32. La estrategia de gestión de seguridad de la información de mi compañía está alineada con su estrategia de negocio.
1 2 3 4 5
Afirmación 33. La estrategia de gestión de seguridad en sistemas de información de mi compañía está alineada con su estrategia de negocio.
1 2 3 4 5
Afirmación 34. La gestión de riesgos de mi compañía proporciona una ventaja competitiva.
1 2 3 4 5
Afirmación 35. La seguridad de la información de mi compañía proporciona una ventaja competitiva.
1 = Estoy completamente en desacuerdo con esta afirmación
2 = No estoy de acuerdo con esta afirmación
3 = No estoy de acuerdo ni en desacuerdo con esta afirmación
4 = Estoy de acuerdo con esta afirmación
5 = Estoy completamente de acuerdo con esta afirmación
Por favor seleccione únicamente una respuesta por afirmación. Todas las afirmaciones siguen la misma escala.
Afirmación 36. La gestión de riesgos de mi compañía proporciona valor a todos sus grupos de interés (sus stakeholders).
1 2 3 4 5
Afirmación 37.La seguridad de la información de mi compañía proporciona valor a todos sus grupos de interés (sus stakeholders).
1 2 3 4 5
Afirmación 38. En mi compañía, los riesgos se gestionarán de una forma más coordinada.
1 2 3 4 5
Muchas gracias por sus respuestas. Son de gran valor para este estudio. Si desea recibir un resumen del resultado de este estudio antes del final de 2006, por favor introduzca una dirección de correo electrónico. Las respuestas al cuestionario no se asocian con la dirección de correo proporcionada.
Acknowledgements
Professor Jean-Noel Ezingeard has played a key role in this study. He has led me throughout the whole elaboration process of this study.
All 82 survey respondents provided a valuable input for this study.
All 82 survey respondents provided a valuable input for this study.
Copyright
Copyright (c) 2006 Alberto Partida.
Permission is granted to copy, distribute and/or modify this document
under the terms of the GNU Free Documentation License, Version 1.2
or any later version published by the Free Software Foundation;
with no Invariant Sections, no Front-Cover Texts, and no Back-Cover
Texts. A copy of the license is available at the GNU
Free Documentation License site.
Permission is granted to copy, distribute and/or modify this document
under the terms of the GNU Free Documentation License, Version 1.2
or any later version published by the Free Software Foundation;
with no Invariant Sections, no Front-Cover Texts, and no Back-Cover
Texts. A copy of the license is available at the GNU
Free Documentation License site.
Subscribe to:
Comments (Atom)












